BitRaser Virtual Machine Eraser

BitRaser Virtual Machine Eraser / 5. BitRaser VM Erasure Configurations
5. BitRaser VM Erasure Configurations
BitRaser Virtual Machine Eraser software allows you to perform the erasure process as per the various configuration for VM host such as Hyper-V and ESXi.
VM Erasure Configurations for Hyper-V
Note: Before proceeding with the erasure process of virtual machine from remote VM host, the following prerequisites must be met for Hyper-V environment:
-
Static IP: To connect to the remote VM host, the static IP address of the remote system is required to establish the connection with the application.
-
Firewall Disabled from Remote Side: The firewall on the remote VM host must be disabled.
-
Port 445 Open: Ensure that port 445 is open.
-
Real-Time Protection Off: Disable any real-time protection on the remote VM host machine that could interfere with the remote connection.
-
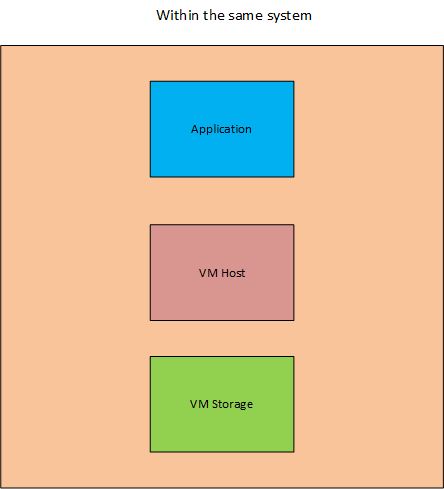
Within the Same System: The application, host, and virtual machine storage are all located within the same system.
-
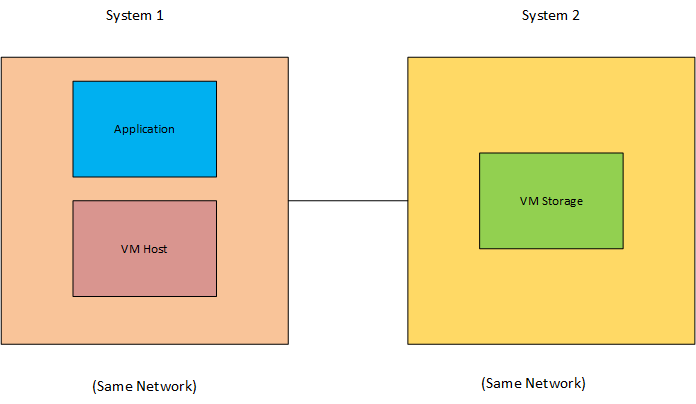
Same Network Setup: Two systems are within the same network, with the application and host located on primary system, while the virtual machine storage is located on an another system within the same network. This allows the erasure process to target virtual machine data stored on the second system over the shared network.
-
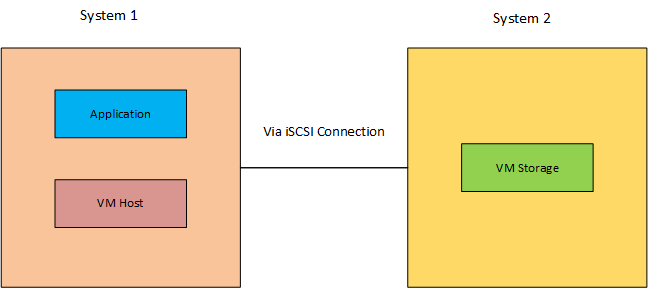
Via iSCSI: Two systems are within range, with the application and host located on same system, while the virtual machine storage is on an another system accessible via iSCSI Initiator Services. iSCSI allows the software to access storage on the remote system over a network, providing a flexible solution for erasure.
-
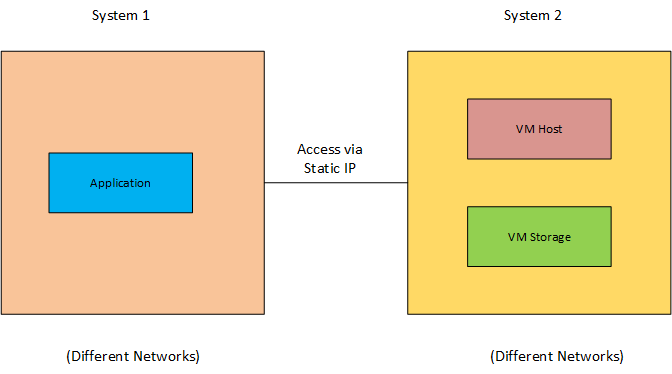
Different Network, Access through static IP: Two systems are in range and accessible with each other but not on the same network, with the application running on the primary system and the VM host and virtual machine storage on a remote system accessible via static IP address. This configuration enables remote erasing across many networks.
-
Multi-System Architecture: This is a setup where three systems are involved. The application is installed on the primary system, the VM host is located on the second remote system, and the virtual machine storage resides on the third system. The primary system communicates with the second system using the static IP address, while the second system accesses the VM storage on the third system via static IP / iSCSI / mapping.
%20new.png)
VM Erasure Configurations for ESXi
Note: Before proceeding with the erasure process of virtual machine, the following prerequisites must be met for ESXi environment:
-
Enable Secure Shell (SSH) Service: Enable the secure shell service on the ESXi host web console to establish the connection with the application.
-
Enable ESXi Shell Service: Enable the ESXi shell service on the ESXi host web console to establish the connection with the application.
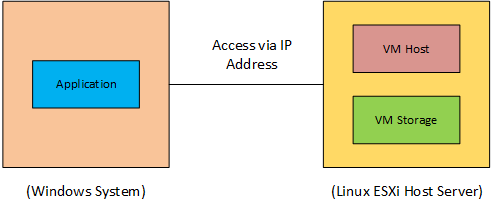
- Windows to ESXi via IP: The application is installed on a Windows system, while the VM host and virtual machine storage reside on a Linux ESXi host server. Windows system and Linux ESXi host server will be accessible to each other via IP address.
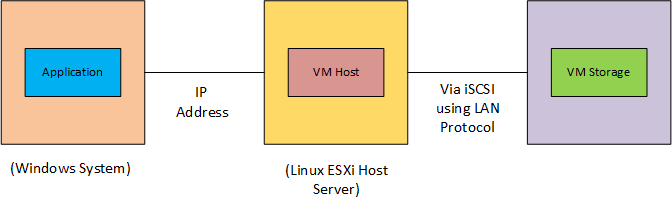
- Multi-System Architecture: In this configuration, The application is installed on the windows system, the VM host is located on the Linux ESXi host server, and the virtual machine storage resides on the third system. The windows system communicates with the Linux ESXi host server using the IP address, while the Linux ESXi host server accesses the VM storage via iSCSI using LAN protocol.
 3. Getting Started
3. Getting Started