In an era where data privacy and data protection have become paramount, organizations are confronted with an escalating need to strengthen their data management strategies. Within this context, the practice of media sanitization assumes a pivotal role in guaranteeing the secure and permanent destruction of sensitive data. Effective media sanitization can be achieved by two primary methods: logical destruction of data or physical destruction of the storage media. The efficacy of logical destruction, or data erasure, relies on adherence to internationally accepted data erasure standards.
Although a multitude of data erasure standards exists, many highly revered ones, like the NIST SP 800-88 and the DOD 5220.22, have either become outdated or are on the verge of obsolescence in the context of newer age devices, embedded data storage chips & other data bearing IOT devices.
To address these challenges and to counter the transformative landscape of data storage, the Institute of Electrical and Electronics Engineers (IEEE), through its Cybersecurity and Privacy Standards Committee, developed the IEEE 2883 Standard for media sanitization. The IEEE Standard for Sanitizing Storage was approved by the IEEE board on June 16, 2022, and was officially published on their website on August 17, 2022.
Why was IEEE 2883 -2022 Standard Developed?
ICT (Information and Communication Technology) systems collect, process, store, and transmit data through various storage systems. From the initial stage of data collection to the final step of data disposal, ensuring effective and efficient data management is a major concern for ICT system owners and data custodians alike. Once these storage devices reach end-of-life, become obsolete, or have to be transferred, resold, or repurposed it is essential to perform storage sanitization to securely remove sensitive data.
According to IEEE, Storage Sanitization or Sanitization, “Refers to the general process of denying access to data from storage media, such that reasonable assurance exists that the data cannot be retrieved or reconstructed.” Here, the interesting point is that if data is not accessible and cannot be destroyed other steps have to be employed like destruction of the storage media.
Therefore, IEEE developed the standard to provide guidance and help organizations better understand sanitization methods. The scope of the IEEE 2883 standard is as follows, “This standard specifies methods for sanitizing logical storage and physical storage, as well as for providing technology-specific requirements and guidance for the elimination of recorded data.”
Although, the use of the IEEE standard is voluntary, complying with it helps organizations maintain accountability in managing their digital assets properly and promoting responsible disposal practices.
What are the Elements of Sanitization as per IEEE 2883?
Sanitization is an integral part of the organizational data governance program that includes various policies and procedures w.r.t the handling of sensitive data. This sensitive data may include personal data, personally identifiable information, electronic healthcare records, trade secrets, intellectual property, customer records, financial records, or mission-critical data, etc.
A major aspect of data governance involves handling the complete data lifecycle and the ICT infrastructure associated with this data. Wiping data from storage systems is important due to evolving business needs or regulatory compliance. Documentation may be maintained to serve as evidence that appropriate action was taken to eradicate data from all devices.
According to IEEE, to make the data permanently inaccessible and eradicate it, one of the following can be used:
| Sanitization |
Description |
|
Data Sanitization
|
Focuses on eliminating all instances of stored data, regardless of their location. These data instances can exist within applications, cloud services, virtual environments, primary compute and storage resources, secondary and offline storage, archives, and data protection systems.
|
|
Storage Sanitization
|
Focuses on data stored within ICT infrastructure that uses nonvolatile storage, like fixed-block storage arrays, NAS systems, object storage, cloud storage, and backup systems.
|
|
Media Sanitization
|
Focuses on data stored on storage devices or storage media.
|
Now, let’s discuss the sanitization methods and techniques that can be used for removing data from storage systems.
Sanitization Methods and Techniques:
IEEE Std 2883-2022 defines three methods that can be employed for sanitizing physical storage, namely, Clear, Purge, and Destruct. These methods use techniques that depend on the type of storage media being sanitized and the data sensitivity.
| Method |
Description |
Technique Used |
Remarks |
|
Clear Sanitization
|
It uses logical techniques to wipe data from all addressable locations to protect against non-invasive data recovery attempts. Typically used for low-sensitivity data.
|
|
Not advisable for sensitive data, as it doesn't erase data from non-addressable locations.
|
|
Purge Sanitization
|
It uses logical and physical techniques to wipe data from all addressable and non-addressable locations, making data recovery through laboratory techniques impossible and leaving the storage device ready for reuse.
|
- Overwrite
- Block Erase
- Cryptographic Erase
- Degaussing
|
Degaussing is a data destruction method for magnetic storage media only and makes the device unusable. It cannot be used on SSDs or NVMe.
|
|
Destruct Sanitization
|
The method employs physical techniques to destroy the media device, making data recovery through laboratory techniques impossible and rendering the device non-reusable.
|
- Disintegrate
- Incinerate
- Melt
|
These techniques can release hazardous materials and pollute the environment.
|
The method used is also dependent on the level of security required by that information and the impact it can have if disclosed to an unauthorized party.
| Security Level |
Impact |
Method |
|
Low
|
Mild
|
Clear
|
|
Medium
|
Moderate
|
Purge
|
|
High
|
Severe
|
Destruct
|
The flowchart below illustrates how IEEE 2883 structures the sanitization process, showing the steps, retries, and fallback options between Clear, Purge, and Destruct.
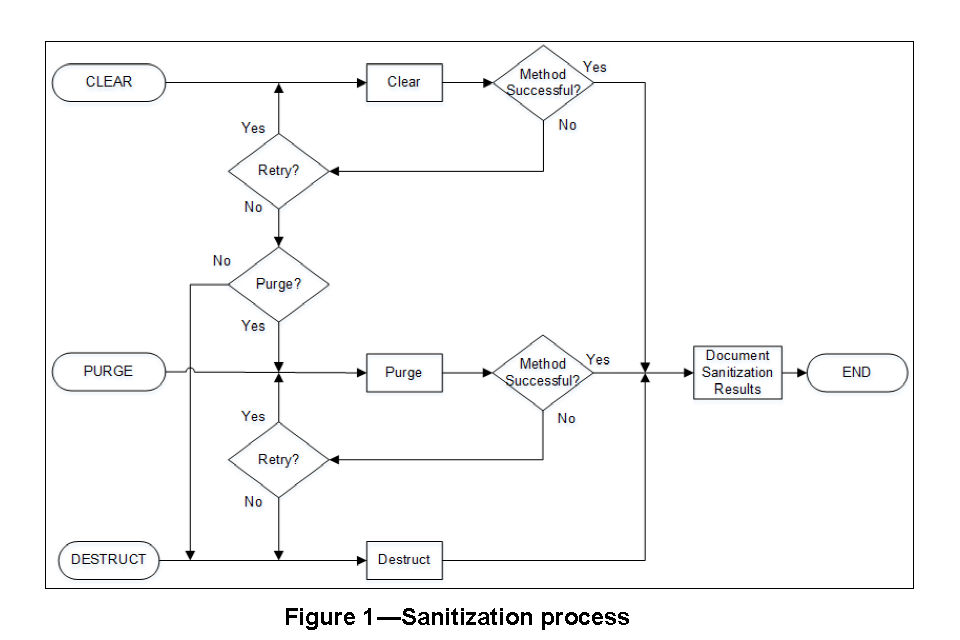
Image Source: IEEE 2883:2022 Standard for Sanitizing Storage
Note: Sanitization methods can fail for various reasons. IEEE Std 2883-2022 recommends attempting alternative methods and, if necessary, moving to higher-level methods. For Example, if the Clear method fails, Purge can be used as an alternative.
IEEE standard, however, does not address requirements for proof of sanitization or requirements for verification of sanitized storage. It says that for audit purposes, verification can be done, and likewise, records of destruction can be maintained for compliance purposes.
Clear & Purge Data Sanitization Methods:
IEEE Clear & Purge are effective methods for ensuring the permanent removal of data from storage media. Each method serves a specific purpose in securely removing data from different types of storage media.
- Overwrite: It is a method that applies to both Clear & Purge, although specific requirements vary. This technique entails replacing the target data with random patterns or characters, effectively sanitizing the storage media. It leaves the storage media in a state that is immediately reusable.
- Block Erase: It is a method applicable to both Clear & Purge. It is performed by issuing the ‘format’ or ‘sanitize’ commands through the host interface. Large regions of storage areas known as “Erase Block” can be wiped out in a single command.
- Media-based Cryptographic Erase: It is an IEEE Std 2883-2022 Purge method used on electronic storage media that contain encrypted data. By changing or sanitizing the encryption key, this technique ensures only the ciphertext remains on the storage media, effectively sanitizing the data.
- Degaussing: It is an IEEE Purge method that employs a Degausser device. The degausser generates a strong magnetic field which, when applied to magnetic storage media, effectively sanitizes them.
|
Sanitization Technique
|
Clear
|
Purge
|
Applicability
|
Limitations
|
Remarks
|
|
Overwriting
|
Overwrite every addressable location on electronic storage media.
|
Overwrite every addressable and non-addressable location.
|
It can be used on most electronic storage media.
|
Not suitable for damaged or non-rewritable storage media.
Erasing a large-capacity device can be time-consuming.
|
The number of overwrite passes or values varies depending on the type of storage device.
|
|
Block Erase
|
Erases large regions of semiconductor storage media called ‘erase block’, in a single operation.
|
Command options to block erase all accessible and inaccessible erase blocks containing user data.
|
Generally used on semiconductor-based storage media like NAND Flash.
|
Most standard storage devices, by default, don’t support the ability to erase individual blocks of data directly.
|
Block erase is generally faster than overwriting for storage devices with a large storage capacity.
|
|
Cryptographic Erase
|
Not applicable.
|
Changes the encryption keys, leaving only cipher text on the storage media, thereby sanitizing the data.
|
Works on Storage media that support encryption, and the encryption key resides in the storage media only and can be changed in a single operation.
|
Requires a strong encryption algorithm and key entropy strength of at least 128 bits.
|
Encryption must be enabled before storing data on the storage media.
All copies of encryption keys must be sanitized.
Erases data quickly as only the encryption key is sanitized.
|
|
Degaussing
|
Not applicable.
|
Magnetic storage media is exposed to a strong magnetic field that disrupts recorded magnetic patterns using a degausser. SSD cannot be degaussed.
|
Works only on magnetic storage media.
|
The magnetic strength required for effective sanitization depends on the device being degaussed.
Low-strength degaussers can leave partially erased areas on the media that can be recovered.
Degaussing renders the storage device unusable.
|
Degaussing requires understanding the appropriate field strength for each storage media type.
It is effective for purging damaged storage media, diskettes, and
high-capacity storage media.
|
Verification of Sanitization:
Verification of the storage sanitization outcome involves assessing the results of the sanitization process to ensure effective sanitization of the storage media. Verification can be a crucial element in the data sanitization program as it can help identify errors or anomalies. The process of verification differs according to the sanitization method used.
- Clear: To verify the sanitization outcome, the storage device interface can be used with representative sampling. It involves selecting and verifying at least 5% of the total addressable space to evaluate the effectiveness of the sanitization process.
- Purge: Full verification of the sanitization outcome must be done using the device interface. In case cryptographic erase was employed, verification may not be possible. However, it is advisable to attempt simple verification by reading the storage media location with known contents and verifying the sanitization process.
- Destruct: Only a physical inspection of the destroyed storage media can be done to verify the sanitization process.
Sanitization Methods for Different Storage Media:
Choosing the correct sanitization method according to storage media is crucial for preventing data recovery and unintentional disclosure. As storage media evolve, using outdated data sanitization techniques can be risky. Sanitization techniques have to be carefully matched to the storage media type. For Example, emerging magnetic storage technologies have higher coercivity and many degaussers do not possess adequate magnetic force to degauss them.
The table below lists different storage media types and the sanitization methods that can be used to sanitize them.
| Storage Media Type |
Examples |
Techniques: Description |
Remarks |
|
Hard copy
|
Papers
Microfilms
Microfiche
|
Destruct: Shred, Pulverize, Disintegrate, Burning
|
Shred or disintegrate paper to smaller than 1 * 5 mm size.
Burn microfilms and reduce them to ash.
|
|
Optical Media
|
CD
DVD
Blu-ray
|
Destruct: Shred, Incinerate, Disintegrate
|
For CD, remove the information layer using an optical disk grinding device.
Incinerate optical disk media
Optical Disk shredders or disintegrators to reduce to particles with a surface area of 0.25 mm2 or smaller.
|
|
HDD, SSHD, and SSD
|
PATA
SATA
Parallel SCSI
SAS
USB
PCIe
RDMA
NVMe
|
Clear: Overwrite, Block Erase
Purge: Overwrite, Block Erase, Cryptographic Erase
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, overwrite data using organizationally approved overwriting tools.
For Purge, use overwrite, cryptographic erase, or block erase.
|
|
Other Magnetic Media
|
Floppy disk
Floptical
SyQuest
LS-120
|
Clear: Overwrite
Purge: Degauss
Destruct: Disintegrate, Incinerate, Melt
|
For Clear, overwrite using organizationally approved software, and then verify. Overwrite with at least a single pass with a fixed value.
For Purge, use an organizationally approved degausser.
|
|
USB Removable Media
|
Pen Drives
Flash Drives
Thumb Drives
Memory Sticks
|
Clear: Overwrite
Purge: Block Erase, Cryptographic Erase
Destruct: Incinerate, Melt, Disintegrate
|
USB storage devices are SSD devices using the SCSI command host interface. The applicable methods for sanitization would be similar to those used for SSDs.
|
|
Memory Cards
|
SD
SDHC
Compact Flash
Memory Stick
|
Clear: Overwrite
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, overwrite using organizationally approved software, and then verify. Overwrite with at least two passes with a pattern in the first pass and its complement in the second pass.
Purge is not applicable however organizationally approved Purge method can be used.
|
|
Embedded Flash Devices
|
Motherboards
Network Adapters
|
Clear: Reset to Factory Settings
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, if the device supports then it should be reset to the original factory settings.
Purge is not applicable.
Electronic boards from the systems should be destroyed.
|
|
RAM & ROM
|
DRAM
|
Purge: Keep without power for 5 Minutes
Destruct: Incinerate, Melt, Disintegrate
|
For Purge, power off and removed the device from the power source and storage device.
|
|
EAPROM
|
Purge: Chip Purge
Destruct: Incinerate, Melt, Disintegrate
|
For Purge, a full chip purge is to be performed as per the manufacturer's data sheet.
|
|
EEPROM
|
Purge: Overwrite
Destruct: Incinerate, Melt, Disintegrate
|
For Purge, overwrite using organizationally approved software, and then verify.
For Destruct, some media are not specifically addressed, but the standard can be used as a valuable resource for making decisions.
|
|
Networking Devices
|
Routers
Hubs
Switches
|
Clear: Manufacturer Reset
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, perform a full manufacturer reset.
For Purge, most devices don't support it; refer to the manufacturer to identify if it is supported.
|
|
Equipment
|
Copier
Printer
Fax
|
Clear & Purge: Manufacturer Reset
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, perform a full manufacturer reset
For Purge, most devices don't support it; refer to the manufacturer to identify if it is supported.
This equipment may contain removable storage media, so the method must be applied according to the storage device type.
|
|
Devices with built-in storage
|
Phones
Tablets
Media Players
Watches
Gaming Consoles
|
Clear: Factory Reset
Purge: Overwrite, Block Erase, Cryptographic Erase
Destruct: Incinerate, Melt, Disintegrate
|
For Clear, use organizationally approved methods like factory reset. The removable storage media can be wiped using the appropriate method.
For Purge, use vendor-specific Purge techniques, or if supported, then overwriting, block erase & cryptographic erase can be used.
|
Conclusion:
As technologies advance and new threats emerge, it's crucial to stay up-to-date with current practices related to data disposal. It is essential always to prioritize security when disposing of any electronic device that has stored sensitive or confidential data.
The IEEE 2883-2022 Standard for Sanitizing Storage provides a useful framework for organizations to securely dispose of their data. Properly sanitizing storage devices can help prevent unauthorized access and protect sensitive information from falling into the wrong hands. While there are multiple methods available to sanitize storage, organizations must carefully consider which method best suits their needs in terms of effectiveness, applicability, data-wiping capability, and compliance with industry standards and regulations.










