Data Destruction has been an integral part of the “knowledge
cycle” that shaped human awareness and wisdom through the ages. Through the information
acquisition, assimilation, synthesis, and distribution stages in this iterative
cycle— data destruction allowed
securing the redundant and secretive information from exposure by obliterating it beyond reversal.
Put simply, data destruction is an ongoing
process emerging from the germinal need
to maintain the privacy and confidentiality of individuals and institutions
by preventing leakage or theft of their information.
You
may want to read Chapter 1: What is Data
Destruction of our Data Destruction knowledge series to get a deeper
understanding of data destruction fundamentals and its origins.
This Chapter focuses on why data destruction is gaining prominence, i.e., the fundamental reasons
driving the urgency of data destruction in the present industrial backdrop.
Data destruction started gaining prominence
with rapid advancements in information creation and processing methods and, in
tandem, the developments in data storage technology. In the late twentieth
century, these advancements necessitated innovations in data destruction
technology to eliminate digital information stored on diskettes, hard disk
drives, solid-state drives, optical disks, memory sticks, etc. Unlike the use of
paper shredder for destroying physical records (mechanically), the growingly
complex digital storage media demanded sophisticated (memory-level) approaches
to attaining data destruction.
Data
Destruction: Key Drivers
While the
aforesaid technological evolution was picking up pace, data destruction also came
to the fore as a top-tier “industrial need.” A few overarching reasons drive
the demand and importance of data destruction, as follows:
1. Rapid Proliferation of Data
The prodigious growth of data is a crucial driver
for data destruction. Digital data is growing at a phenomenal pace across every
dimension volume, variety, and velocity - shaping the “big data” realm.
The IDC Data Age 2025 report informs that the global datasphere (i.e., total data created, captured, and replicated) will grow from 33 Zettabytes 1 in 2018 to 175 ZB by 2025 at a CAGR of 61%. This digital data is stored at the Core (traditional and cloud data centers), the Edge (enterprise-hardened infrastructure), and the Endpoints (PCs, smartphones, and IoT devices).
[1] 1 ZB = 1 Trillion Gigabytes
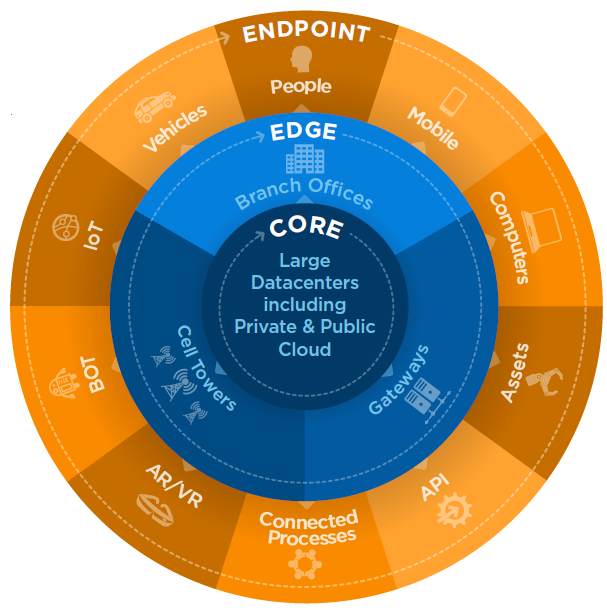
Global Datasphere: Core, Edge, and Endpoint
Image Credit : cs.rpi.edu
As per the IDC report, this global datasphere
is complex to fully secure against data threat vectors due to its continuous
interaction with the physical world at the 'edge' and ‘endpoints.' Moving
between the Core (data centers) and Endpoints (client machines) through the
Edge (enterprise infrastructure), this data is stored on billions of individual
user & commercial devices, including computers, storage drives, servers,
etc.
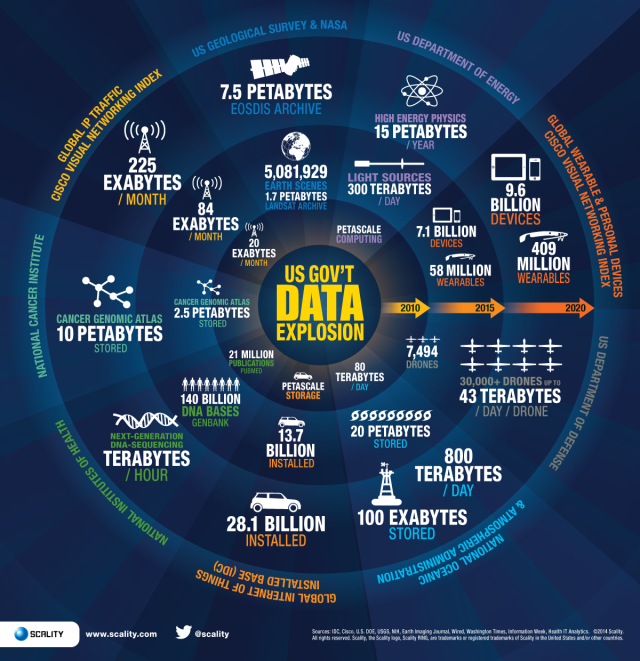
Expanse of Data Storage Devices
Image Credit : whatsthebigdata.com
Typically, cybersecurity measures are taken to
protect this data throughout its “active usage” stages, i.e., when the information
is used for its intended purposes, like drawing customer or market insights,
making a business decision, personalizing a message, business reporting, etc.
However,
what happens when this data becomes redundant and unwanted, missed out from procedural
accounting, abandoned, archived, or neglected because it is not needed? At this
stage, this data comprising sensitive information is beyond the purview of
cybersecurity measures and the typical IT surveillance and is, therefore,
vulnerable to exposure, leakage, and theft. The various
contingencies emerging in the data lifecycle stages can result in a data breach
with myriad implications.
Revisiting
these data lifecycle challenges at a highly magnified (big data) scale,
involving zettabytes of digital information, immediately underscores the
importance of data destruction.
2. Cumulative Count of Storage Hardware
Complementing the data explosion trend, the growing
aggregate count of installed or in-use storage hardware also underpins the need
for data destruction. For example, Statista informs[2] [3] that approx. 5.2 billion hard disk drives and 3.3 billion PCs (laptops and
desktops) were globally shipped between 2010 and 2020. Likewise, about 13.8 billion smartphones were
shipped worldwide between 2009 and 2021.
Further, as per Statista Data Storage Insights [4], the global spending on
Hosting, Storage, and computing market is expected to surpass US$ 163 billion
by 2021. And, Data Storage Units market, valued at US$ 78 billion, is expected
to constitute a whopping 47.8% share of this total market!
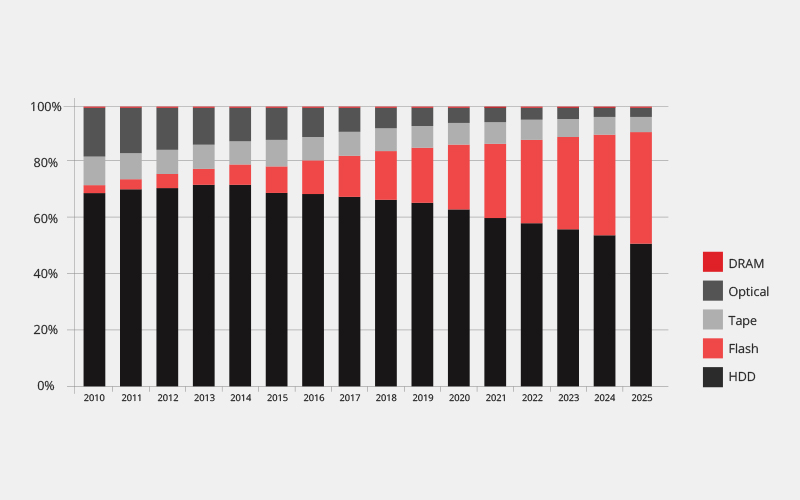
Byte Shipment Share by Storage Media Type
[Source: IDC Data Age 2025 study]
[2] Statista hard drives
shipment stats
[3] Statista desktop and
laptop stats
[4] Statista data storage (statistics
& facts)
These
trends indicate a high “cumulative count” and demand for data-bearing devices that
might be transitioning through different lifecycle stages, namely— acquisition,
allocation, usage, reallocation, return, resell, donation, and disposal. These lifecycle
stages change the storage devices’ ownership and potentially expose the
underlying data to the new owner if it is not destroyed beforehand.
For example, internal reallocation of IT assets
such as laptops, workstations, and mobile devices involves reassigning the used device to a new
user. In this case, the previous user’s data stored on the reallocated device is
vulnerable to unwanted exposure if it is not destroyed beforehand.
Similarly, an organization auctioning used
storage devices such as workstations, servers, and smartphones to a reseller without data
destruction is at imminent risk of exposing sensitive information. The
situation can culminate in a data breach incident, haunting
the company several years down the line!
Therefore, the devices invariably require
a systematic approach to destroy and eradicate the data throughout their
lifecycle stages. Please refer to the section on Revisiting Industrial
Context for data leakage threats at different lifecycle stages of
storage hardware.
3. Enactment of Data Protection Laws
The passing of focused legislations to protect individuals’
data privacy and confidentiality is a singular development bringing data
destruction to industrial eminence. While data privacy laws, such as the US
Privacy Act of 1974, have been in force for decades, modern legislation such as
EU-GDPR and CCPA brought tremendous focus on data protection and consumer data privacy.
As per the United
Nations Conference on Trade and Development, 128 out of 194
countries have legislation in place to secure the data privacy of individuals.
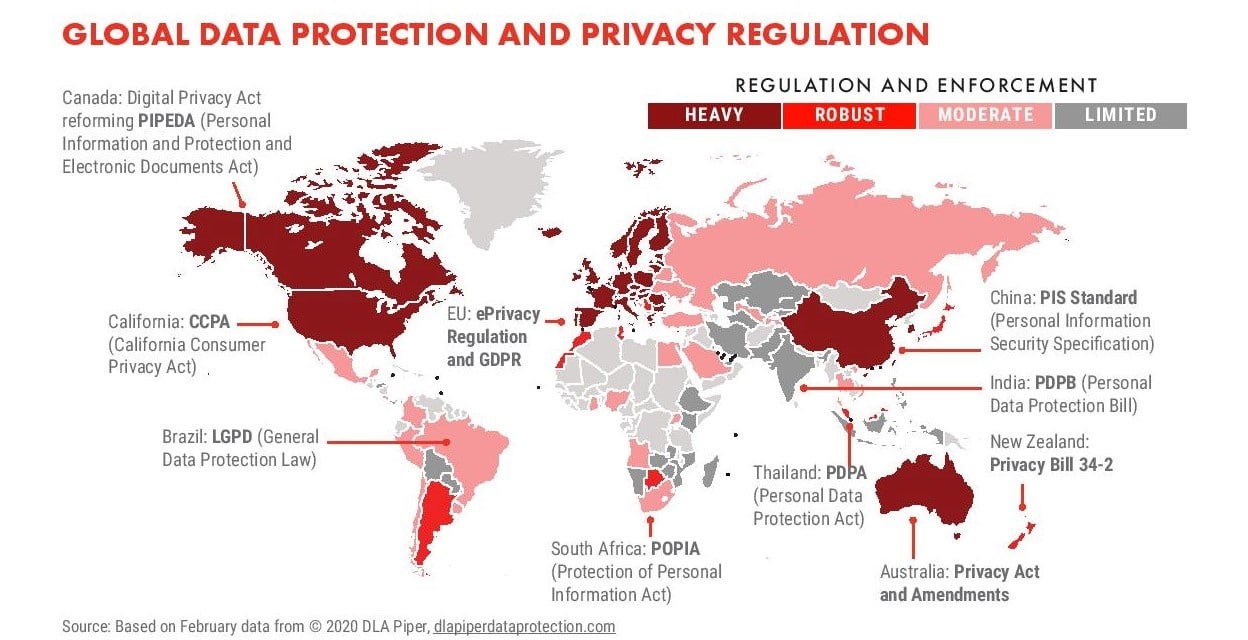
Image Credit: headerbidding.co
These laws formulate overarching mandates to
protect individuals’ privacy and obligate organizations, including commercial
entities, government institutions, and non-profits, to adhere to the norms.
Broadly, each of these laws has provisions that
mandate organizations to destroy the personal data in their possession, based
on inputs such as user consent, authorized storage duration, etc. These laws
empower users to exercise rights such as “right to erasure,” “right to be
forgotten,” etc.
Further, with broad jurisdictional scope, many
of these data protection laws, such as GDPR, CCPA, NY SHIELD Act, etc., bring
overseas entities operating in the home territory or possessing the residents’
data into their purview. By scaling the geographical boundaries, these
overarching legislations accentuate data destruction as a “global need” —
wherever data is being created and stored (and that is virtually everywhere).
Failure
to comply with modern data protection laws can attract significant financial
penalties, litigation, and even imprisonment due to direct violation of the rules
or data breach incidents resulting from inadequate data destruction.
Generally,
the financial implications of data breach incidents,
resulting because of no or insufficient data destruction, can be exorbitant.
Revisiting
the Industrial Context
Another way to understand the growing relevance
of data destruction is through real-world industrial scenarios involving ongoing
data and IT hardware lifecycle management. As mentioned earlier, storage
devices traverse lifecycle stages viz. acquisition, usage, reallocation,
return, resell, donation, disposal, etc.
A majority of these stages demand explicit data
destruction checkpoints for the permanent removal of redundant information. Furthermore,
without data destruction, there are practical risks of data leakage and theft,
outlined in the following scenarios:
Scenario
1: Inventorying hard drives and computers
Your organization might store the old IT
hardware, including PCs and hard drives, in a warehouse before offloading them
for downstream recycling. Such devices, inventoried without data destruction,
continue to carry sensitive data of previous users. Imagine if a hard drive or
laptop goes missing from the warehouse due to any reason like theft, misappropriation,
or accounting error.
The situation on the face of it looks like
(only) hardware loss, but it can culminate in a data breach incident with enormous implications if
the data on the storage media is compromised. This
looming threat of data breach persists until you destroy the data. Be aware
that it takes just one hard drive. You might not find it missing in a vast lot until
it’sC

Scenario
2: Disposing storage hardware after formatting or resetting
IT asset management professionals usually
format the storage drives or reset computer systems to factory settings before
disposing them. Deletion, formatting, and resetting are often mistaken as
methods to eliminate or remove data, whereas, the fact is, these methods do not
remove the data. They either remove the references or prepare the device for
fresh use. The data remains inside the storage media in a residual state,
vulnerable to illegal extraction or recovery until you destroy it.
A lab
study of the world’s largest known sample of 311 used devices,
including hard drives, smartphones, and memory cards, had established this
residual data threat due to incorrect or inadequate data destruction. The study
revealed that 7 out of 10 devices in the test sample had residual data,
establishing a lack of data destruction awareness and its correlation with data
breach possibilities.
Image Credit: evernex.com
A few other real-world IT asset management
scenarios that can turn out in data breach incidents without data destruction
include the following:
Scenario
3: Returning leased computers and servers- Without data
destruction, the rented devices might expose sensitive information to the broker
or vendor.
Scenario
4: Auctioning used storage hardware to resellers - A batch of data-bearing devices can
land up with a reseller or ITAD vendor, posing risks of large-scale data
leakage if the data is not destroyed before releasing the devices’ custody.
A few
years ago, PBS.org had reported an incident wherein a hard drive salvaged from
the e-wasteland of Agbogbloshie in Ghana was put up for sale in the open market
for a few dollars. The hard drive, reportedly belonging to a large military
contractor, stored sensitive information on multi-million dollar US government
contracts.
Scenario
5: Donating old computers to charity - While meeting CSR
responsibilities, an organization may fail to destroy the existing information on
the donated devices before handing them over to the beneficiary. This situation
can expose the organization’s sensitive data to the new user or a random person
downstream when the device is recycled or dumped.
Scenario
6: Internal reallocation of devices - Another seemingly harmless
data leakage situation may crop up with the reallocation of a laptop or desktop
PC without data destruction. The previous user’s data might remain recoverable
even after hard drive formatting or resetting the PC, potentially exposing
confidential information.
Need for
Data Destruction: Financial
Implications
The costs incurred due to data
breaches provide an incisive perspective to the mounting need for data
destruction. According to IBM Cost of a Data Breach Report 2020[1], the global average total
cost of a data breach is US$ 3.92 million, with United States having the
highest average cost of data breach, equaling US$ 8.19 million. Companies need
to bear this high cost of data breach, resulting due to leakage of undestroyed
information, on account of multiple implications, namely:
1.
Fraudulent
transactions
Leakage of sensitive
data such as banking credentials, credit card details, income tax records,
credit records, social security numbers, etc., can lead to unauthorized
financial transactions. Commonly, these include credit card frauds, siphoning
of funds, exploitation of credit history, etc.
For businesses, spurious
transactions could mean massive damages in indemnities, such as chargeback
requests from consumers. For example, the average cost of credit card fraud[1] for the merchant equals
$200 per compromised cardholder. And, this damage is in addition to the
financial penalties imposed by data-protection laws for a reported data breach
incident.
2.
Hefty
legal penalties
Data protection laws
have provisions for initiating legal proceedings, including class-action lawsuits,
for data breach incidents, culminating in financial penalties. These fines can
be substantial, arrived at based on the organization’s annual turnover or in
multiples of the violation instances (number of affected individuals).
For example, GDPR violation
can draw a penalty of €20 million or 4% of the annual global turnover,
whichever is higher. In contrast, CCPA imposes a fine of US$7500 per deliberate
violation and US$2500 per inadvertent violation. Likewise, Nevada Privacy Law
has provisions to sanction civil action and penalties of up to US$5000 per
violation. And, the NY Privacy Act of 2021 proposes a fine of up to $15,000 per
violation.
3. Reputation
loss and customer alienation
Failing to destroy data
can result in a data breach and consequently affect a company’s customer base
because of the loss of trust, bad publicity, and brand damage. Based on the
quantum of the breach and the number of affected customers, customer alienation
can be significant with a direct and long-term impact on revenue.
According to a PCI Pal
survey[1], 83% of consumers in the
US expressed that they will not buy from a business for several months after a
security breach incident, while 21% of customers said that they would abandon
the company forever. The survey also found that 58% of consumers in Canada were
hesitant to do business with a company for several months after a breach.
Data
Destruction is an Indispensable Need
Data destruction has been a recurrent theme in
the knowledge cycle, which gained top-tier priority with the growth of data and
storage media. The shift from physical recordkeeping to digital storage in the
late twentieth century unfurled a colossal challenge — i.e., to constantly
protect the privacy of the snowballing datasphere contained in a vast number
and variety of storage devices transitioning a maze of lifecycle stages.
Data destruction addresses this need well. By
obliterating sensitive information forever, data destruction can secure it from
unauthorized possession or access.
Aside from data and storage devices, regulatory compliance is a critical driver
that underpins the need for data destruction. Data protection laws such as
GDPR, CCPA, and the like impose compliance as a definitive obligation for doing
business, compelling organizations to devise and deploy compliant data
destruction practices.
By and large, the cost of (not doing) data destruction is hefty considering the implications such as legal penalties, fraud transactions, customer alienation, and reputation loss. Further, it can significantly impact organizations’ sustainability by diminishing their shareholder value and enterprise value. Therefore, companies need to take a proactive approach and use appropriate methods and techniques to data destruction that arrives as an eminent need in the data-first world.
Want to gain a deeper understanding of data
destruction methods and techniques to compete in the emergent landscape?
Read Chapter
3: Data Destruction Methods and Techniques of our knowledge series.















