Data destruction has emerged as a top-tier industrial need considering the surfeit of data, storage devices, and strict governance of data protection laws & regulations globally. Data destruction holds a prominent place in data lifecycle and IT asset management. Broadly, there are two categories of data destruction methods - physical and logical. Organizations can decide on the appropriate method based on data classification, sensitivity of information, and type of storage media while taking sustainability, device reuse, and the circular economy into consideration.
Types of Data Destruction Methods
There is no cookie-cutter solution, and data destruction methods vary for every organization to fit their objectives and requirements. While for highly sensitive data related to national security, it is recommended to physically destroy the IT asset, business critical confidential data can be logically erased with the help of a software-based data erasure. Since the appropriate method of data destruction depends on several factors like the sensitivity of data, regulatory compliance requirements, the type of storage media, logistics, cost considerations, and environmental impact, the responsibility of figuring out what’s right lies on the shoulders of the business and not the service providers.
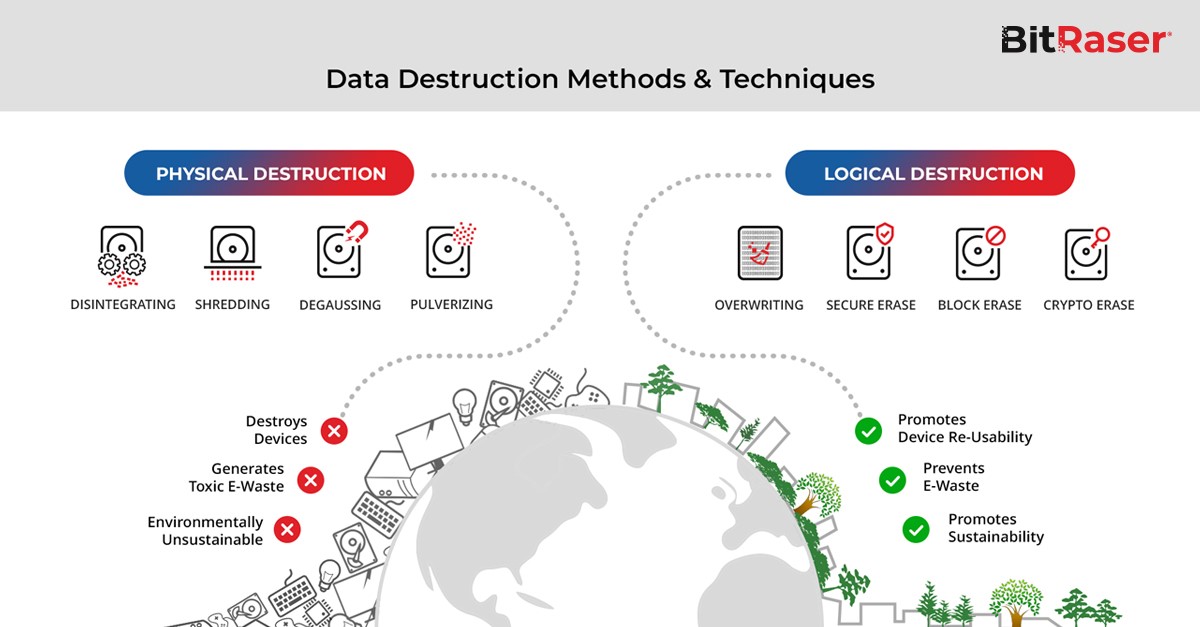 Image: Methods of Data Destruction
Image: Methods of Data Destruction The different types of physical and logical data destruction techniques are explained below.
1. Physical Destruction
This approach is based on destroying the storage media such as hard drive platters, flash memory chips, USB flash drives, mobile phones, optical media, IoT devices, point-of-sale devices, etc. The approach uses "brute force" to obliterate the physical hardware, thereby rendering the media and the underlying data inaccessible. Disintegrating the hard drive platter, shredding the storage media into pieces, or destroying the fundamental property of storage media instead of physically destroying it are some of the common methods of data destruction. There are some methods such as cutting, crushing, bending, and melting which neither prevent data leakage nor salvage the storage media. A defining characteristic of the physical data destruction method is that every technique renders the storage media useless, and turns it into e-waste which ends up in landfills.
The NIST SP Rev 1 800-88 guidelines mention an emergency procedure that involves the use of a firearm to shoot a hole through the media device. However, since many sections remain unharmed with this technique, risks of data recovery still remain. Below are some of the methods of physical destruction:
- Shredding: It disintegrates the storage media using specialized equipment such as a shredder. It breaks down (shreds) the storage media like the drive platter along with the electronic and mechanical components into minute pieces, in dimensions as small as 2 mm. The data stored on the media is destroyed as a result of physical disintegration.
 Image: Hard Drive Shredding
Image: Hard Drive Shredding
Degaussing: This approach is based on neutralizing the magnetic field or polarity of magnetic storage media by applying an external magnetic field of opposing polarity. A sufficiently strong magnetic field disorients and demagnetizes the local magnetic domains used for storing data on the media, resulting in data destruction. The process is called demagnetizing and the equipment used is called a degausser.
A degausser applies a stronger magnetic field of higher coercivity than that of the target magnetic media to rearrange or randomize its field orientation. It can degauss a limited number of drives at once. For effective degaussing, precise matching of the degausser"s strength vis-à-vis the media coercivity is crucial. Although, it can work on non-functional or dead hard disk drives, degaussing is not an adequate method of data destruction for SSDs and hybrid drives. The NIST SP Rev1 800-88 Guidelines also suggest against relying on degaussing as a reliable data destruction method: "Existing degaussers may not have sufficient force to degauss evolving magnetic storage media and should never be solely relied upon for flash memory-based storage devices or magnetic storage devices that contain non-volatile non-magnetic storage." The UK's national technical authority, National Cyber Security Centre (NCSC) does not approve the use of degaussers, and advises businesses to defer to NSA for product approvals.
 Image: Hard Drive Degausser
Image: Hard Drive Degausser
Readers can refer to the article on "Does degaussing work on SSDs" to understand the pitfalls of degaussers.
- Pulverizing: The process involves the application of an external force on the physical media to elastically deform and crack it into smaller pieces, thereby destroying the media like hard drives or SSDs. Unlike shredding, it grinds drives into finer particles for higher security. Pulverizers are often used by the military due to the need of maintaining higher security levels.
- Disintegrating: This technique is more advanced than shredding, breaking down the storage media into fine particles (less than 2mm x 2mm) or powder. NSA-approved disintegrators are recommended for high security destruction of sensitive data. The process may be slower due to fine grinding.
- Incinerating/Burning: The storage device is put into a licensed incinerator and burned at high temperatures to reduce it to ashes. Due to the release of GHG emissions, this technique is highly discouraged. Also, modern devices like SSDs or flash drives may survive extreme heat.
A majority of physical data destruction methods cannot be performed on-premises. Shipping the data-bearing IT assets from remote locations to offices or ITAD facilities increases the risk of data breaches which can take place in the absence of a secure chain of custody. Not only that, many physical destruction methods produce toxic waste, combustion products, and similar hazardous materials. For example, incineration produces chemical compounds called dioxins that damage air, water, and soil. Apart from causing cancer, it can also cause hormonal, developmental, and immunity-related issues. Further physical destruction renders the device unusable and security may be compromised due to the data recovery possibility from even smaller shredded drive particles.
2. Logical Destruction: This method directly overwrites the data at the "memory level" by implementing specific techniques on the storage locations, including the user addressable area, Host Protected Area (HPA), and Device Configuration Overlay (DCO). HPA is a hidden area on the memory, which is invisible to the Operating System (OS) but can be accessed using specialized tools and commands. DCO is a hidden area on disk drives, which is inaccessible through BIOS or OS but it can be accessed using specific commands & tools. Alongside overwriting, logical data destruction methods also include Block Erase, Secure Erase (SE), and Cryptographic Erase (CE). These methods and their usage are highlighted in NIST SP Rev 1 800-88 guidelines and IEEE 2883 guidelines.
- Overwriting is the most prevalent technique that destroys the existing information by replacing it with random characters like 0s, 1s, etc. The technique is implemented using specialized data rewriting algorithms to destroy data on magnetic disks (HDDs), flash-based memory drives (SSDs, NVMe, M.2, USB, etc.), hybrid drives, mobile phones, Mac devices, laptops, PCs, Chromebooks, etc. Also known as data wiping or data erasure, overwriting is a software-based technique that renders a device reusable unlike any physical destruction method. Data erasure is feasible on any functioning storage device that supports read/write commands from a host computer system through interfaces such as Serial Advanced Technology Attachment (ATA), Parallel ATA, Small Computer System Interface (SCSI), etc. Overwriting can be performed using a single pass or multiple passes to destroy the target data on all user-addressable memory locations of a drive. According to the NIST SP Rev 1 800-88 guidelines, “a single overwrite pass with a fixed pattern such as binary zeros typically hinders recovery of data even if state of the art laboratory techniques are applied to attempt to retrieve the data.”
- Block Erase is the technique associated with semiconductor-based storage media such as NAND flash memory-based SSDs. Unlike SSDs, magnetic media like hard drives cannot be block erased due to their design and command limitations. Block erase method can erase a large-capacity storage media in one go while taking less time than overwriting.
- Secure Erase (SE) uses the ATA standard command SECURITY ERASE UNIT to overwrite data stored on the media. This firmware-based erasure method is often optimized for the device architecture like ATA or NVMe. NIST highlights that SE is not applicable to storage media with SCSI interfaces. It can be performed in two modes – normal and enhanced. While the former applies READ NATIVE MAX or READ NATIVE MAX EXT to address data present in Logical Block addressing (LBA 0) and replace them with 0s or 1s; the latter ensures everything including unused reallocated sectors.
- The Cryptographic Erase technique erases or replaces the Media Encryption Key (MEK) of storage media including drives with hardware encryption like SSDs & Self-Encrypting Drives (SEDs), thereby rendering the data in the form of ciphertext, which is illegible. The technique does not destroy the data but only destroys the encryption key. So, its efficacy depends on the robustness of the SED’s encryption algorithm. However, it may carry risks like -
- Decryption of the sanitized media using a backup key saved elsewhere.
- Unauthorized access to data that was stored in unencrypted form.
The sanitization commands for Secure Erase and Cryptographic Erase vary based on factors like media type and support for encryption.
Performing data erasure with a logical data destruction method enables device reuse. Using logical data destruction method, organizations can either reuse the erased devices, donate to an NPO/NGO for CSR objective, or resell after an upgradation cycle. These IT assets can then enter the usage cycle, promoting sustainability, and contributing to the circular economy.
How to Choose the Best Data Destruction Method
Choosing the right data destruction method depends on various factors. A few key factors are given below:
Criteria |
Shredding |
Degaussing |
Overwriting |
Definition |
Physically destroys storage device by shredding it into smaller pieces. |
Physically destroys the fundamental property of the drive by disrupting the magnetic field. |
Erases data by writing random patterns on the drive and makes it usable |
Data Sensitivity |
Not recommended for highly-sensitive data due to the possibility of forensic recovery from shredded particles as per NIST. |
Suitable for highly classified data on magnetic media only with a high coercivity NSA-approved degausser. |
Best for highly sensitive data when done correctly without any interruption. Suitable for almost all storage media like HDD, SSD, USB, NVMe, M.2, hybrid drives, mobile devices etc. |
Cost Consideration
|
Expensive.
Costs of shredders, shredding services, and logistics – all are high.
|
Expensive.
NSA-approved degaussers are expensive with attached technical expertise costs.
|
Cost-Effective Solution.
Software-based erasure is extremely low in comparison to degaussing or shredding with no technical expertise required.
|
Onsite/Offsite/Remote |
Onsite & Offsite -possible to perform within the organization or at a third-party service provider facility. |
Offsite or Onsite if degaussers are purchased. |
Data erasure can be performed Onsite, Offsite, or Remotely. |
Health & Safety Impact |
Release of toxic materials like lead and cadmium. |
Pulse & Coil degaussers carry health hazard due to exposure to strong electrical charge. |
No Health and Safety Hazard. |
To know more about the detailed comparison of data destruction techniques w.r.t other parameters, refer to Data Destruction Techniques: Choose the Best for You.
However, a question still remains: how do you adopt these techniques to make them serve your real-world needs? As organizations become more environmentally-conscious, they set new ESG goals, and carbon emitting data destruction techniques create hindrances in this mission. To ensure data privacy without damaging the environment, organizations should form a comprehensive data destruction policy.
What should a secure data destruction policy include? Read Chapter – 4 on Data Destruction Policy of the Knowledge Series to learn more.