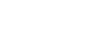Data destruction is the process of destroying sensitive information that was stored digitally on systems or devices like magnetic tapes, disk drives & other storage media. Destroying digital data means rendering the data inaccessible or unreadable so that it cannot be reconstructed. Data destruction does not imply deletion, formatting, or factory resetting. It is to be noted that when data is deleted, it is neither destroyed, erased, nor sanitized. In data deletion, the pointers to the data are removed, making the data hidden. Deletion marks the used spaces as ‘free’ while the data remains intact until it is overwritten. However, this data can easily be recovered using freely available data recovery tools. Clearly, for organizations processing sensitive data, data deletion is ineffectual. The appropriate choice of data destruction for organizations and individuals which aim to permanently remove their confidential information, will depend upon the storage media being used.

Often, data destruction, data sanitization, and data erasure are used interchangeably, but they have distinct meanings and implications in the context of data security and regulatory compliance.
- Data Sanitization permanently removes or destroys the data from the storage media so that it becomes irretrievable even with the advanced forensic data recovery techniques. NIST Special Publication 800-88 Rev 1. Guidelines for Media Sanitization states that sanitization makes the data on the storage media infeasible for a given level of effort. Physically destroying the storage media or performing logical sanitization on it will ensure data is permanently removed from the storage media. Logical sanitization methods include data erasure and cryptographic erasure.
- Data Erasure is a subset of data sanitization. It is different from data destruction because it involves the use of a software-based tool that overwrites the existing data with zeroes and ones, or random patterns thus making data unrecoverable. As per the NIST standard, the process of software-based data erasure must be verified by following the ‘Random’ and ‘Total Verification' methods. Certified data erasure tools generate tamper-proof reports or certificates of erasure, which provide verifiable proof for audits and compliance requirements.
Many media sanitization guidelines and standards, like ADISA ICT Asset Recovery Standard 8.0, provide the same definition for these three terms. However, all of them refer to different processes.
For guidance on data destruction, standards like the above-mentioned NIST media sanitization guidelines and ISO/IEC 27001 can be referred to.
The Evolution of Storage Media & Its Impact
Understanding the roots of data recording systems provides us context for why today’s data destruction methods have evolved alongside storage technologies. Data destruction is a fascinating subject that might seem like a freshly carved inquiry in today’s data-first realm, but it is indeed an ancient domain -about 6000 years old! As a need and a practice, it has existed since the birth of data and recordkeeping several millennia ago. However, it has evolved into more refined and targeted forms, keeping pace with innovations in data recording and storage technology.
The modern storage media technologies capable of storing data in terabytes and gigabytes are the result of a long journey of consistent development. Far from being simple and automated, older storage media didn’t store data on a click; it was bulky and occupied physical space. It took a long duration to store and retrieve data and required special skills to use. The evolution of storage media began in the early 1800s.
- Early 1800s: In 1804, Joseph Marie Jacquard had invented an attachment with which any loom could weave desirable patterns of cloth automatically. This attachment used punched cards to control the weaving process, automating the weaving looms as a result. This technology was later used in the 1830s by Charles Babbage to use punch cards as an input-output medium in the Analytical Engine. Herman Hollerith, the American statistician, developed a tabulating machine that electronically read and sorted punched cards to record data. It was used in the 1890s to process census data.
- 1950s Onwards: With the 1950s came the magnetic drum memory, called Atlas. Coated in ferromagnetic material and cylindrical in shape, it rotated while getting circled by read and write heads in order to store data. Magnetic tape played a significant role in the computer revolution in 1951, enabling the storage of mass information. The focus grew more on making data storage media faster, easier, and with larger capacity in the years that followed. From magnetic disks, floppies, semiconductors, and integrated memory chips to CDs, Solid State Drives (SSDs), flash memory, and cloud storage, storage media has become easily affordable and accessible. With each leap in storage technology, new risks emerged w.r.t. accessibility, portability, reusability, and data destruction.
Data, Storage Media, and Data Destruction
With the growth in volume and variety of data and ample options of storage media being available, the dangers to data privacy also grow manifold. The reusability of today’s storage media, including SSDs and HDDs, introduces a high risk of data breaches if data destruction is not performed thoroughly before devices are repurposed or reused. Additionally, modern storage media have become highly portable due to their compact size. However, securely erasing data from these miniaturized components in media such as flash drives, has become increasingly complex. This makes it crucial to ensure that confidential data is permanently erased before it can be exposed or misused.
That also implies selection of an appropriate data destruction method because one method cannot be effective on all types of storage media. The choice of data destruction technique directly impacts both security and sustainability. Physical data destruction guarantees irretrievability but produces e-waste and sacrifices asset value. Logical destruction or data erasure, on the other hand, sustains hardware lifecycle, enables reuse and aligns with circular economy objectives.
The inherent nature of digital data stored on reusable media paves the way for data overwriting, replacement, and removal-based approaches for data destruction. These approaches are based on executing specific commands via the host computer interface to overwrite and replace the addressable memory locations on a hard drive (or other reusable media) with binary patterns. This overwriting process if executed properly, can destroy the existing data and turn it irretrievable.
Read Ch-3 Data Destruction Methods and Techniques of the BitRaser Knowledge Series on data destruction to learn more about this in detail.
Balancing Security, Compliance, and Sustainability
As the amount of data organizations handle continues to grow and regulations get stricter, businesses are under growing pressure to not only destroy data securely but also do it in an environmentally responsible way.
Organizations that are committed to sustainability as part of their ESG goals need to prioritize logical data destruction over physically destroying their IT assets. Data destruction software can help permanently remove data and also enable asset reuse. Bringing back the devices into the usage cycle indirectly impacts the manufacturing rate of new IT assets, reducing CO2e emissions generated by the production of new devices.
That said, not all organizations have the liberty to reuse old devices. Highly regulated industries like defense and banking process classified information which is highly sensitive. In these cases, physical destruction such as shredding or degaussing is often necessary to eliminate all risk. Still, one smart step remains: performing data erasure first adds an extra layer of protection before the hardware is physically destroyed.
As the need to balance data security, regulatory compliance, and sustainability grows, data destruction no longer remains a backend IT function. Instead it's becoming a strategic decision. Let’s explore Data Destruction Gaining Eminence?