The NIST SP 800 88 R2 Guidelines for Media Sanitization was published by the National Institute of Standards and Technology on September 26, 2025. This is a revised version of NIST SP 800-88 Rev.1. As per the abstract of the official document, this guide “will assist organizations and system owners in setting up a media sanitization program with proper and applicable techniques and controls for sanitization and disposal based on the sensitivity of their information.”
It introduces several changes to revision 1, and includes media sanitization recommendations that accommodate the modern-day information storage media (ISM). ISM is the digital representation of devices that store bits and bytes, unlike hard copy, which is the physical representation of information in the form of paper printout, platens, microfiche, etc. ISM can be volatile and non-volatile storage, including RAM, ROM, hard disk drives (HDDs), flash memory, phones, networking devices, and systems providing virtual/logical storage such as cloud storage.
The key components of NIST 800 88 Rev.2 are defined below.
3.1. Sanitization Methods
NIST 800-88 R2 defines two sanitization techniques (logical and physical) and three sanitization methods (clear, purge, and destroy). Each of these methods can have technology-specific sanitization techniques.
In logical techniques, over an interface, software or a tool is used to either replace data, eliminate data by issuing specific commands, or eliminate access to the data. The protection of confidentiality can vary according to the specific technique. The purpose of logical sanitization is to ensure that the ISM remains usable. Physical techniques are performed by applying external physical measures to either eliminate the data or the ISM (storage media). These involve some form of destruction, and most of them leave the media in an inoperable condition.
3.1.1. NIST Clear Sanitization Method
The NIST Clear method performs logical sanitization techniques by applying read and write commands to the ISM in user-addressable storage areas. The techniques include replacing the original target data with new non-sensitive data. If rewriting is not supported, then the device is reset to the default factory state. This method sanitizes data from these locations, safeguards data from non-invasive data recovery techniques, and does not affect the usability of the storage media.
NIST 800 88 R2 advises against using multiple (1-39) overwrite passes to sanitize data from Hard Disk Drives (HDDs), as earlier used to happen when complying with DoD 5220.22-M. The application of a clear method varies for different storage media; many devices like mobile phones and office equipment can only be reset to the default factory state. Since the factory reset deletes the pointers to the files, making the retrieval of cleared data infeasible, it satisfies the requirements of the clear sanitization.
NIST 800 88 Rev2 warns of the probability of unintentional data disclosure risks with the use of Clear on modern-day storage media, including magnetic drives and flash-memory-based media.
3.1.2. NIST Purge Sanitization Method
In Purge, physical or logical techniques are applied to the ISM to render data recovery infeasible. These techniques vary according to storage media. They include block erase, cryptographic erase (CE), degaussing, etc.
Carefully choosing a purge sanitization technique can help preserve the storage device for future use. Many devices may not support the purge mechanism, although most support Clear. Among logical purge methods, CE stands out for its speed and efficiency in sanitizing target data. However, its effectiveness relies on the quality of the cryptographic implementation and meeting specific prerequisites that are mentioned in Section 3.2.
For degaussing a storage media, the magnetic strength of the degausser must match with the coercivity of the ISM. It is ineffective for flash-memory-based storage devices or magnetic storage devices containing non-volatile, non-magnetic storage. Degaussing faces complications in sanitizing the emerging magnetic storage media technologies, which have higher coercivity. It renders the ISM unusable by damaging it while failing to sanitize the data and is considered a destruction technique for ISM it is ineffective on.
3.1.3. NIST Destroy Method
The destroy sanitization method in NIST R2 renders the storage media (ISM) unusable and data recovery infeasible using state-of-the-art laboratory techniques. Hard copy and information storage media can be sanitized using the destroy technique. However, this technique is not applicable to virtual or logical storage. For virtual storage, the only viable sanitization method is CE.
When both NIST clear and NIST purge are ineffective on the ISM, then destroy is the only sanitization option left. It is to be noted that the storage media is not considered destroyed unless the access to or recovery of target data is infeasible using lab techniques.
Physical destruction techniques:
- Melt: Application of heat to liquefy the storage media, hence destroying it.
- Pulverize: Grinding, crushing, or applying other mechanical means to reduce the storage media to dust or a fine powder.
- Disintegrate: Separating, breaking, or decomposing the storage media into constituent small particles, parts, or elements.
- Incinerate: Burning the storage media to ash, resulting in complete destruction.
- Shred: Cutting or tearing the storage media into bits and pieces, destroying the media completely.
The higher the density and hardness of the internal components of the storage media, the tougher it is for certain physical destruction methods to be effective. Partial damage may occur from cutting, bending, or applying emergency procedures, rendering sections of the storage media accessible using state-of-the-art techniques. Pulverization and shredding should be applied to the storage media only if it contains the lowest security categories of data.
3.2 Cryptography Use and Cryptographic Erase
Section 3.2 of NIST SP 800-88 R2 focuses on CE that leverages encryption and key management to render data unrecoverable by sanitizing the cryptographic keys used for encryption. CE is faster and highly assured compared to other methods, particularly when implemented through self-encrypting drives (SEDs) with validated FIPS 140 encryption modules.
However, its effectiveness depends on robust cryptographic implementation, including strong key generation, wrapping, and derivation practices, with algorithms offering at least 128-bit security strength. CE is only applicable when all sensitive data on the storage device has been encrypted; unencrypted (plaintext) data requires other sanitization methods. The standard stresses that CE may not be suitable if encryption keys have been backed up, escrowed, or stored externally, as these could allow for future data recovery. Proper sanitization of all related keys, including wrapping and derivation keys, is essential. To ensure assurance and traceability, organizations must document CE operations in detail, including device specifics, encryption settings, key handling procedures, and error management. This detailed recordkeeping supports both compliance and confidence in the sanitization process.
NIST defines the complete cryptographic operation, its applicability, sanitization of keys, etc., as per the sections below.
Section 3.2.1. Strength of Cryptography for CE
Section 3.2.2. Applicability of CE
Section 3.2.3. Sanitization of Keys
Section 3.2.4. Quality of Cryptographic Implementations
Section 3.2.5. Traceability of CE Operations
4. Media Sanitization Program
NIST 800 88 Rev. 2 references ISO/IEC 27040, which recommends making storage sanitization a component of the organization’s data governance process. A storage sanitization program helps in preventing data breaches that may happen due to mishandling of media and helps ensure secure IT asset disposal. This media sanitization program should include:
- Defining policies for storage asset disposal during asset transfers, reuse, or destruction, and specifying minimum acceptable sanitization methods.
- Identification of the scope and sanitization decision criteria.
- Performing storage sanitization according to the defined methods.
- Determination of the adequacy of the sanitization performed.
- Identification of the necessary evidence or documentation required for compliance.
4.1. Storage Sanitization Policy
The presence or absence of a sanitization policy can significantly impact organizations. The policy should be framed keeping in mind the following:
- The data classification scheme should align with acceptable sanitization methods. Data should be categorized based on its level of sensitivity, i.e., low, medium, or high.
- Expected outcomes of storage sanitization activities.
- Proof of sanitization activities.
- Training of personnel involved in sanitization.
- Testing, calibration, and maintenance of sanitization tools.
- Types of assurances that the vendor of the ISM should provide for the ISM’s sanitization capabilities.
4.2. Sanitization Scope
This section covers the scope of media sanitization and emphasizes that whole-media sanitization is preferred over partial or selective methods due to verification challenges. It highlights the use of CE for partial sanitization but notes that its effectiveness depends on vendor implementation and data storage locations.
4.3. Storage Sanitization and Disposition Decision Framework
This section covers the framework for making risk-based sanitization decisions while taking into consideration data confidentiality level based on FIPS 199, media type, reuse plans, organizational control, and data protection requirements.
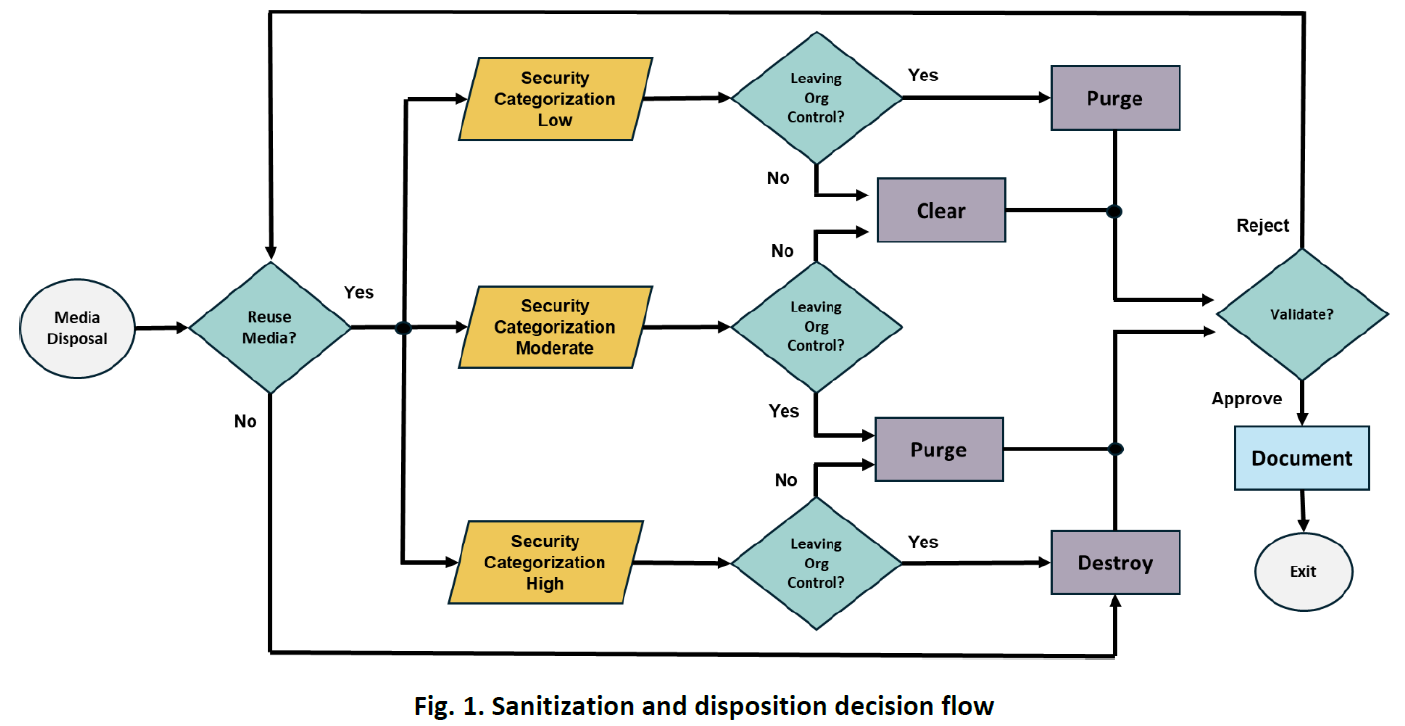
Image: Sanitization and Disposition Decision Flow Source: NIST SP 800-88 Revision 2
4.4. Performing Sanitization
This section covers the execution of media sanitization according to chosen methods, Clear, Purge, or Destroy, while complying with standards like IEEE 2883, NSA/CSS Policy 6-22, and NSA/CSS Policy Manual 9-12.
Individuals performing sanitization should consult ISM manufacturer recommendations and additional guidance, including DISA Security Technical Implementation Guides (STIGs), for additional guidance.
4.5 Sanitization Assurance
According to ISO/IEC 27040, verification of the effectiveness of the sanitization process is a crucial part. To determine the adequacy, the results of sanitization techniques are inspected. In case of unacceptable outcomes, the sanitization is repeated. When the outcomes are as expected, the sanitization is acceptable. For repeated sanitization, storage media should be rechecked, as prior erasure may have rendered it unusable.
- Sanitization Verification (4.5.1): This process determines the outcomes of the sanitization technique. To verify if the sanitization technique was successful, the sanitization results are inspected. While for destructive methods, the remnants are inspected, for non-destructive methods, sanitization verification depends on the type of ISM. NIST SP 800-88 R2 states that after performing Clear or Purge techniques, there is no need to conduct elaborate ISM sampling of contents unless required by the organization.
- Sanitization Validation (4.5.2): To ensure that the target data was successfully sanitized, validation is required to approve the sanitization as effective or reject it for being ineffective. On rejection, the process is repeated using a different sanitization technique or a more secure sanitization method. An analysis of the identified errors, or risks to data confidentiality, should be done. In case the data confidentiality risks are unacceptable, then the sanitization should be considered insufficient.
Factors affecting the sanitization effectiveness:
- Inaccessible sections of the ISM despite it appearing to be fully functional.
- Selecting a sanitization method that is inappropriate for the ISM or the data’s security category.
- Use of unapproved sanitization equipment or tools, or unskilled personnel performing the sanitization.
- The sanitization operation does not meet the minimum requirements.
- The scope of sanitization is too narrow, like performing simple overwriting to an ISM (like SSD) that employs overprovisioning, resulting in a significant amount of data left unchanged.
Both sanitization outcome and data sensitivity are considered when validating sanitization.
4.6. Documentation
For each sanitized ISM, a certificate of sanitization is required. The certificate can be in the form of a physical or electronic record. In cases where physical access to the ISM is difficult, automatic documentation becomes crucial. Important components of the certificate are listed below:
- Manufacturer
- Model & Serial Number
- Media Type (Physical or ISM)
- Media Source
- Used Tool with Version
- Sanitization Method (Clear, Purge, or Destroy)
- Sanitization Technique (Overwrite, Block Erase, CE, or Degauss)
- Verification Method
- Information of individuals performing sanitization verification & validation, such as name, designation, date, location, contact details, and signature
Conclusion
NIST SP 800-88 Rev.2 introduces an updated approach to media sanitization and emphasizes the development of a media sanitization policy and a media sanitization program. The revision distinguishes between logical and physical sanitization techniques and aligns requirements with modern storage technologies. Rather than specifying individual sanitization methods, Rev.2 recommends adherence to IEEE 2883:2022, NSA standards, or an organization-approved alternative. Organizations previously following NIST SP 800-88 Rev.1 should note that it has been superseded and is no longer applicable, and they should update their internal policies to comply with the current guidelines.










